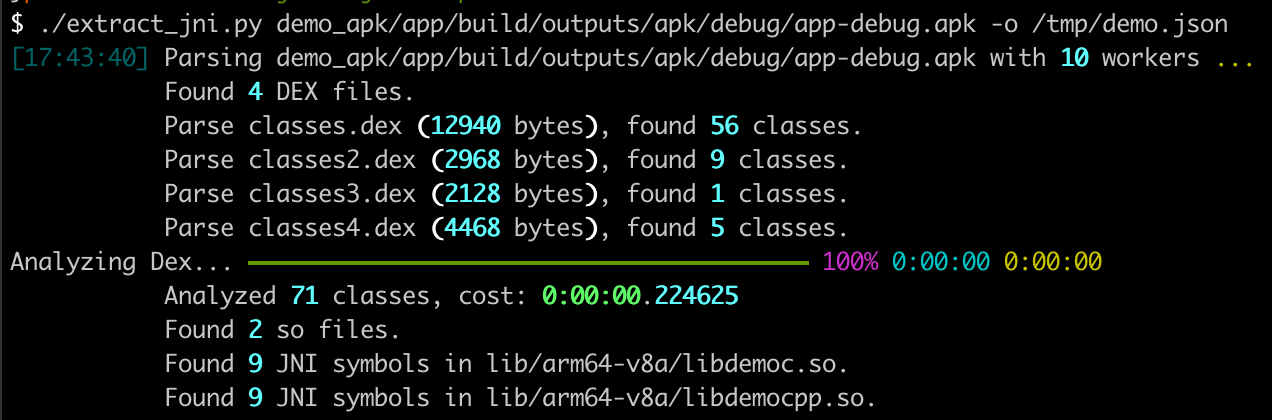
Find JNI function signatures in APK and apply to reverse tools.
- Use extract_jni.py to generate
signature.json - Load
signature.jsoninto Ghidra/IDA/BinaryNinja
Install dependences:
pip3 install -r requirements.txt
Usage:
$ ./extract_jni.py -h
usage: extract_jni.py [-h] [-j WORKERS] [-o OUTFILE] apk
positional arguments:
apk /path/to/apk
optional arguments:
-h, --help show this help message and exit
-j WORKERS parse apk with multiple workers(processes) (default: 8)
-o OUTFILE save JNI methods as formatted json file (default: stdout)Example:
./extract_jni.py app-debug.apk -o signature.jsonSee Ghidra.
| Before | After |
|---|---|
 |
 |
See IDA.
| Before | After |
|---|---|
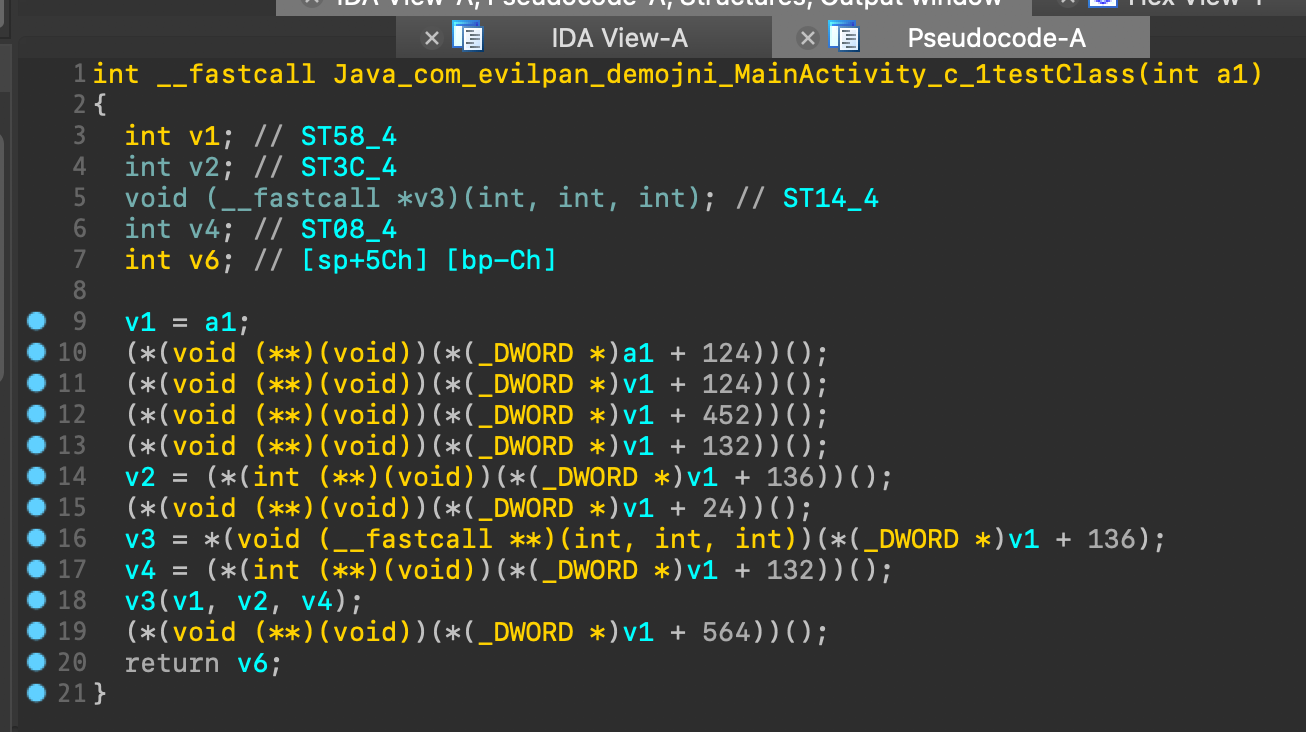 |
 |
see Binary Ninja.
| Type | Image |
|---|---|
| Before |  |
| After |  |
WIP, see Radare2
Tested with demo APK.
cd demo_apk
./gradlew assembleDebug- support both C/C++ JNI functions
- support overloaded JNI functions
- remove Jadx dependence, all in Python
- Add BinaryNinja plugin
- support env->RegisterNatives JNI functions