Caution
This project is under active development and is not recommended for non-technical users at this stage. The installation and usage of Bugbane can be detected by spyware and stalkerware. Do not use it when there is a direct risk of physical harm.
Bugbane is an open-source Android application designed to help potential spyware and stalkerware victims self-triage their own device and, when appropriate, export evidence for later analysis by trusted organizations. Read more and see the demo in our blog post (Italian version).
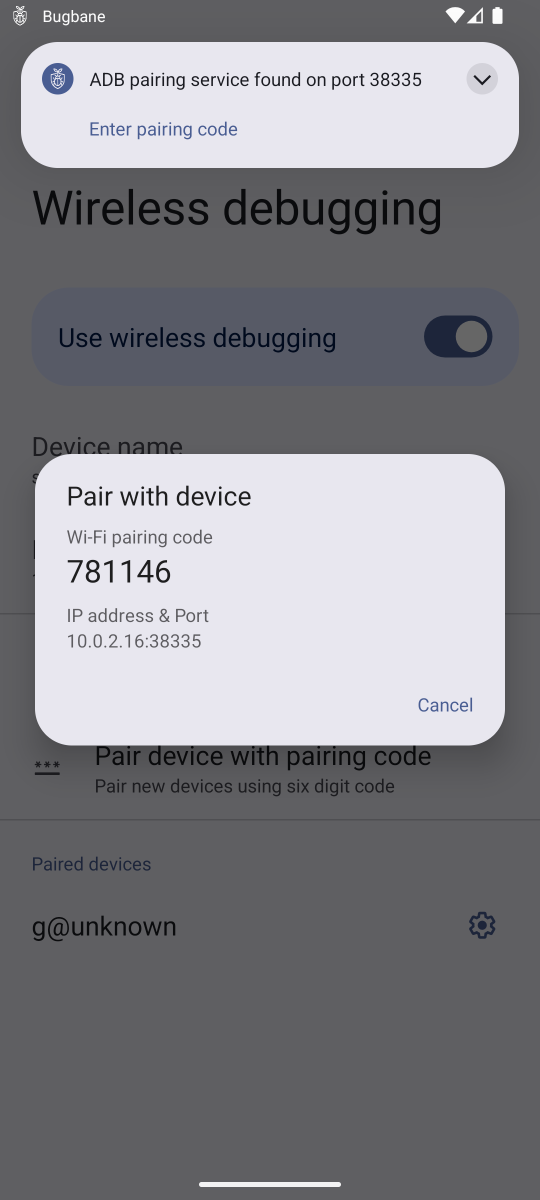
Unlike existing tools such as MVT, Bugbane does not require a separate computer, command-line usage, or debugging skills. It uses ADB Wireless Debugging to issue commands directly to the same device on which it is installed, through a guided, user-friendly interface.
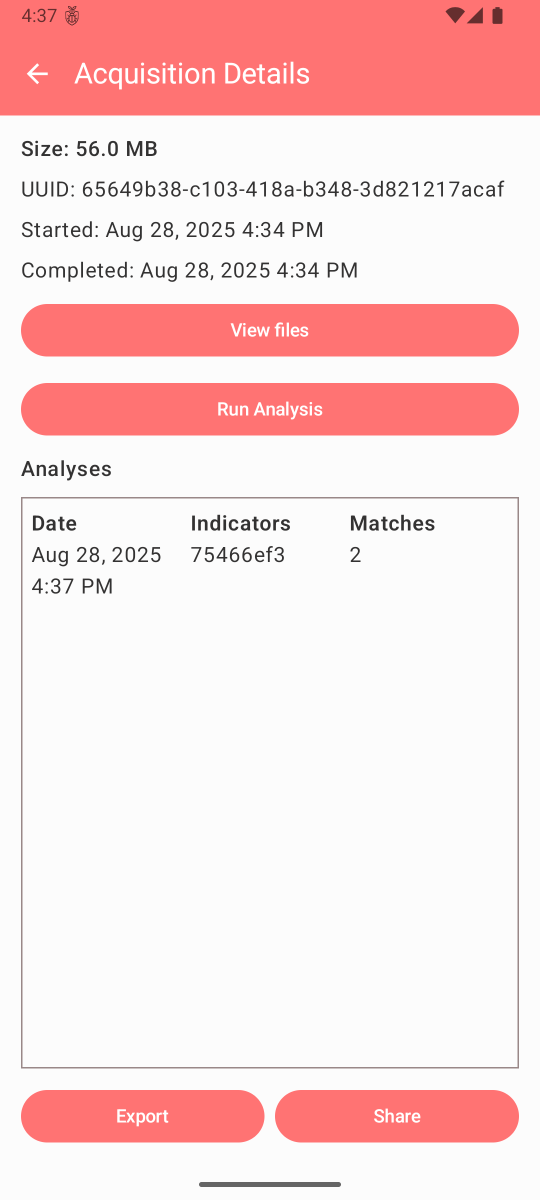
Exports are intended to be AndroidQF-compliant, making them portable and analyzable off-device using existing tools, and can be easily shared via Signal or other communication tools. Each export is automatically encrypted with a random password using age. Since exported data can contain sensitive personal information, the initial scan is performed on-device using a re-implementation of MVT that reuses the same IOCs as the original.
This project is still evolving. A beta release will be announced when ready, and testing will be opened at that stage.
Portions of the code in Shizuku are distributed under the Apache 2.0 License, whereas Bugbane is released under the GNU General Public License, Version 3 (GPLv3).
Bugbane uses the pairing logic from Shizuku, forked and included in our code, and libadb-android as a dependency. This allows it to interact with the device's debugging service exactly as a computer connected via USB would.
- Commands are executed with shell privileges.
- Output is saved to the application’s private storage and encrypted.
- The generated ADB RSA certificate is authorized for debugging and stored encrypted at rest, using StrongBox-backed credentials when available.
Export and sharing logic are currently in progress. Documentation will be expanded as development continues.